Building a Robust Security Posture with Threat Intelligence Platforms
- 1 Understanding Threat Intelligence Platforms
- 2 Key Components of Threat Intelligence Platforms
- 2.1 1. Data Collection and Aggregation
- 2.2 2. Normalization and Analysis
- 2.3 3. Threat Detection and Intelligence Sharing
- 2.4 4. Integration with Security Tools
- 3 Benefits of Using Threat Intelligence Platforms
- 3.1 1. Early Threat Detection
- 3.2 2. Improved Incident Response
- 3.3 3. Enhanced Visibility
- 3.4 4. Strategic Decision-Making
- 4 Challenges and Considerations
- 5 Best Practices for Implementing Threat Intelligence Platforms
- 5.1 1. Define Clear Objectives
- 5.2 2. Integrate with Existing Systems
- 5.3 3. Continuous Monitoring and Updating
- 5.4 4. Training and Skill Development
- 6 Conclusion
Cybersecurity is paramount in today’s digital landscape, where businesses increasingly depend on technology. Cyber threats have evolved, becoming more sophisticated, targeted, and frequent, affecting organizations across various sectors. To mitigate these risks, businesses must establish a robust security posture. Central to this effort is the adoption of Threat Intelligence Platforms (TIPs), which provide the necessary tools to anticipate, identify, and neutralize threats before they escalate into full-blown attacks.
Understanding Threat Intelligence Platforms
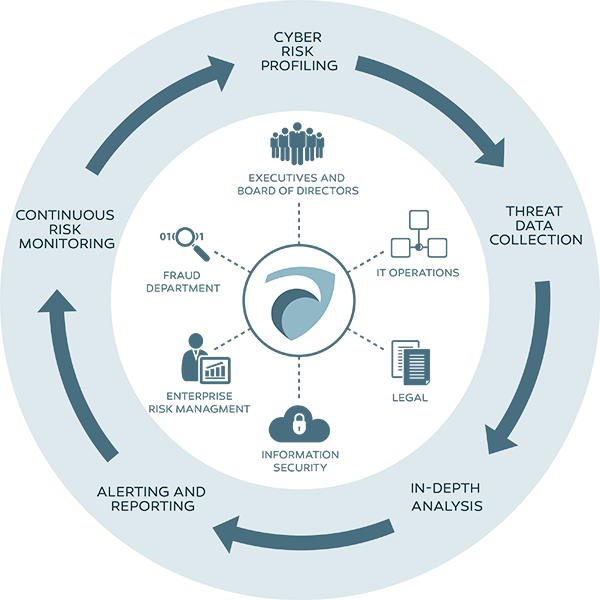
A Threat Intelligence Platform (TIP) is a specialized software solution designed to collect, process, and analyze data related to potential cyber threats. These platforms are the nerve center of an organization’s cybersecurity efforts, providing actionable insights derived from vast internal and external data. TIPs are not merely passive tools; they enable organizations to take proactive measures by predicting and responding to threats in real time.
The Evolution of Threat Intelligence
The concept of threat intelligence has evolved significantly over the years. In the past, organizations relied heavily on basic security measures like firewalls and antivirus software. However, as cyber threats became more complex, the need for a more sophisticated approach emerged. Tips were developed to address this gap, offering a comprehensive solution beyond mere detection and response. They provide context-aware intelligence that helps organizations understand the broader threat landscape, enabling them to make informed decisions about their security posture. Consid
Key Components of Threat Intelligence Platforms

Threat Intelligence Platforms comprise several vital components that work in tandem to provide a holistic view of an organization’s security environment. These components include:
1. Data Collection and Aggregation
The foundation of any TIP is its ability to collect and aggregate data from a wide range of sources. These sources can be categorized into:
- Internal Sources: This includes security logs, network traffic data, incident reports, and endpoint telemetry. Internal data provides insights into the organization’s specific vulnerabilities and past incidents, helping to build a profile of potential threats.
- External Sources: TIPs also draw from external sources such as threat intelligence feeds, security blogs, research reports, and dark web monitoring. These external sources offer a broader view of the threat landscape, including emerging threats and trends that could impact the organization.
2. Normalization and Analysis
Once data is collected, it undergoes a normalization process, converting it into a consistent format suitable for analysis. This step is crucial because data from different sources vary significantly in structure and content. Normalization ensures that the data is compatible and can be effectively analyzed.
During the analysis phase, TIPs employ advanced algorithms, including machine learning and artificial intelligence, to identify patterns, correlations, and anomalies. These insights help detect potential threats, assess their severity, and determine the appropriate response.
3. Threat Detection and Intelligence Sharing
A core function of TIPs is detecting threats before they can cause significant harm. By leveraging machine learning and AI, TIPs can identify unusual behaviors, detect zero-day vulnerabilities, and predict potential attack vectors.
Furthermore, TIPs facilitate intelligence sharing across different teams within the organization. This shared knowledge enables a coordinated response to threats and ensures that all relevant stakeholders are informed and prepared.
4. Integration with Security Tools
Integration is essential to maximizing the effectiveness of a TIP. These platforms are designed to work seamlessly with existing security tools such as Security Information and Event Management (SIEM) systems, firewalls, endpoint protection solutions, and incident response platforms. By integrating these tools, TIPs can automate threat responses, streamline workflows, and enhance the organization’s security posture.
Benefits of Using Threat Intelligence Platforms
The implementation of Threat Intelligence Platforms offers numerous advantages that contribute to a more robust security posture:
1. Early Threat Detection
TIPs excel at identifying threats before they can evolve into significant incidents. By continuously monitoring for indicators of compromise (IOCs) and other warning signs, TIPs allow organizations to take preemptive action, thereby reducing the risk of data breaches and other cyber attacks.
2. Improved Incident Response
When a security incident does occur, TIPs play an essential role in the response process. By providing contextual information about the nature of the threat, the platform helps security teams quickly assess the situation and determine the most effective course of action. This leads to faster resolution times and minimizes the impact of the incident on the organization.
3. Enhanced Visibility
One of the most significant benefits of TIPs is the enhanced visibility they provide into the organization’s security environment. TIPs comprehensively view potential vulnerabilities, attack vectors, and other risks by aggregating and analyzing data from multiple sources. This holistic perspective is essential for understanding the full scope of the threat landscape.
4. Strategic Decision-Making
The insights generated by TIPs are invaluable for making informed decisions about cybersecurity strategies and investments. Organizations can use this intelligence to prioritize their security efforts, allocate resources effectively, and ensure that their defenses are aligned with business objectives.
Challenges and Considerations
While the benefits of TIPs are clear, implementing these platforms is not without challenges. Organizations must be prepared to address the following issues:
1. Complexity
Managing and integrating data from a diverse range of sources can be complex. Organizations need skilled personnel capable of configuring, maintaining, and optimizing TIPs. Additionally, the sheer volume of data processed by these platforms can be overwhelming, making it difficult to extract actionable insights without the right expertise.
2. Cost
The cost of implementing and maintaining a TIP can be significant, particularly for smaller organizations with limited budgets. The investment includes not only the price of the platform itself but also the resources required to manage and operate it effectively. Organizations must weigh the benefits of a TIP against the associated costs to determine if it is a viable option.
3. Data Accuracy and Relevance
The effectiveness of a TIP is highly dependent on the accuracy and relevance of the data it processes. Organizations must ensure that the threat intelligence they rely on is up-to-date, accurate, and relevant to their specific environment. Failure to do so can lead to false positives, missed threats, and an overall decrease in the platform’s effectiveness.
Best Practices for Implementing Threat Intelligence Platforms

To maximize the effectiveness of TIPs and overcome potential challenges, organizations should consider the following best practices:
1. Define Clear Objectives
Before implementing a TIP, organizations should define clear objectives aligning with their cybersecurity strategy. This includes identifying the specific threats they want to address, the types of data they need to collect, and the outcomes they hope to achieve. Clear objectives will guide the selection and configuration of the platform, ensuring that it meets the organization’s needs.
2. Integrate with Existing Systems
To achieve seamless operations, organizations must ensure that their TIP integrates with existing security tools and systems. This integration allows for the automation of threat responses, enhances the flow of information, and ensures that all parts of the security infrastructure work together effectively.
3. Continuous Monitoring and Updating
The threat landscape constantly evolves, so TIPS must be regularly updated with the latest threat intelligence feeds. Continuous monitoring for new threats and vulnerabilities is crucial to maintaining an effective defense. Organizations should also periodically review and update their TIP configurations to adapt to changing circumstances.
4. Training and Skill Development
A TIP’s effectiveness largely depends on the skills and knowledge of the security team. Organizations should invest in training programs that help their teams understand how to use TIPs effectively, interpret the data they provide, and respond to threats promptly. Ongoing skill development is essential to keeping up with the latest advancements in threat intelligence and cybersecurity.
Conclusion
In conclusion, Threat Intelligence Platforms are essential for building a robust security posture in today’s increasingly complex digital landscape. They allow organizations to detect, analyze, and respond to threats in real time, ensuring their defenses remain effective against evolving cyber threats. While implementing a TIP can be challenging, the benefits—including early threat detection, improved incident response, enhanced visibility, and strategic decision-making—make it a worthwhile investment for organizations committed to safeguarding their digital assets. By following best practices and continuously refining their approach, organizations can leverage TIPs to stay ahead of cyber threats and maintain a strong security posture.