Nmap: My Experience with This Powerful Network Scanning Tool
Many IT and cybersecurity experts use the powerful network scanning tool Nmap.
Nmap is a powerful network scanning tool that I’ve found very useful in my job as an IT worker. It lets me scan networks quickly and easily, which helps me find live hosts, open ports, and working services. This post will discuss what I’ve learned and done with Nmap and show you how it can be used in the real world.
What is Nmap?
Nmap, short for “Network Mapper,” is a powerful open-source tool for network discovery and security auditing. Initially released by Gordon Lyon (Fyodor) in 1997, Nmap has evolved into a highly versatile utility that enables users to scan and map network structures. It works by sending packets to various hosts on a network and then analyzing the responses to determine the active devices, their IP addresses, the services they are running, and the operating systems they use.
Nmap’s versatility makes it suitable for various tasks, from routine network inventory to sophisticated security assessments. Its ability to detect open ports, identify vulnerabilities, and discover network services allows administrators and security professionals to understand their network environment better and identify potential weaknesses before malicious actors can exploit them.
Nmap’s functionality extends beyond simple network scanning; it incorporates advanced features that enhance its capabilities. For instance, it supports stealth scanning techniques to avoid detection by firewalls or intrusion detection systems, making it a valuable tool for penetration testing.
Nmap can also perform detailed version detection to determine the specific versions of software running on networked devices, which is crucial for vulnerability assessment. Additionally, its scripting engine, NSE (Nmap Scripting Engine), enables the execution of custom scripts to automate complex tasks, such as detecting malware or checking for specific security vulnerabilities. The tool is widely respected in the cybersecurity community and among network administrators for its robustness, flexibility, and comprehensive documentation, making it an essential component in the toolkit of anyone involved in network management or security.
Why Did I Apply For Nmap?
I found the open-source command-line tool Nmap, which is short for Network Mapper, invaluable for network port and IP address scanning. Although Linux is its main platform, its adaptability spans several others. Nmap helps me to quickly find installed programs and provide a whole picture of the network.
As a network administrator, Nmap lets me find all the devices running on my network, uncover open ports and services, and spot possible weaknesses. Gordon Lyon, sometimes known as Fyodor, developed the program to streamline mapping a whole network and identify its open ports and services. Featuring in films like The Matrix and the TV series Mr. Robot, Nmap has become somewhat well-known throughout the years and even entered popular culture.
Many other security experts find Nmap preferred for several more convincing reasons than other network scanning software. First, Nmap lets you quickly and effectively map networks without requiring advanced instructions or setups. It enables you to create complicated scripts using the Nmap Scripting Engine (NSE) and supports basic commands such as determining whether a host is up.
Nmap Features I Most Find Beneficial
- Nmap fast identifies any device on a network—including servers, routers, switches, and mobile devices. Managing single or numerous networks makes this function quite helpful.
- Nmap can even reasonably detect application versions and find services running on a system, including DNS and web servers. This talent enables me to see current weaknesses.
- Nmap can offer a comprehensive operating system that runs on device information, including particular OS versions. This element is vital when developing further methods of penetration testing.
- Using Nmap to use current scripts from the Nmap Scripting Engine, I search systems during security audits for vulnerabilities. This talent helps me to spot and fix security flaws.
- Nmap also provides Zenmap, a graphical user interface designed to enable visual mappings of a network. This interface helps reporting and increases usability, therefore facilitating the presentation of complex network structures and vulnerabilities to stakeholders.
How To Install Nmap?
The particular requirements of the work will determine the several uses for Nmap. These are some broad Nmap use guidelines:
- Download and set up Nmap from the official website – https://nmap.org/download.html.
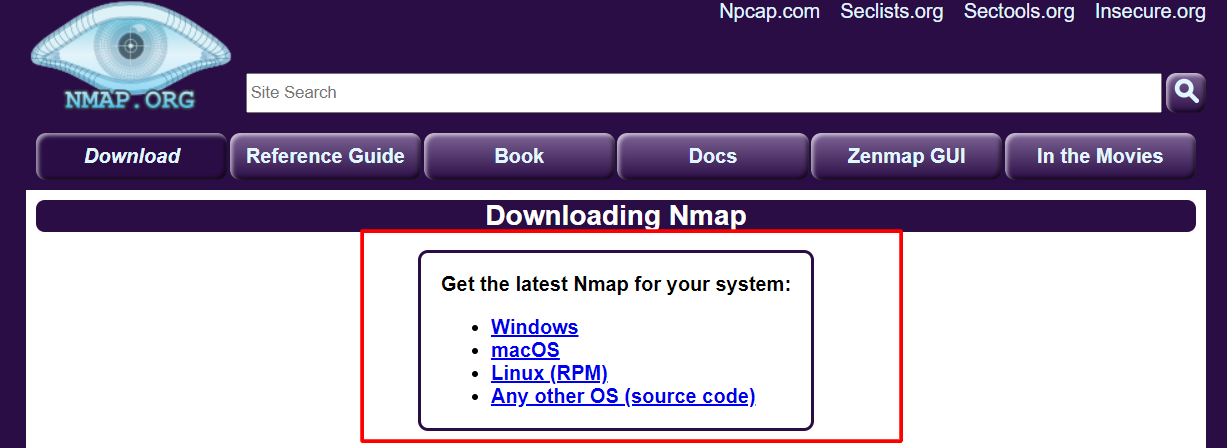
- Check for the executable file that is being downloaded in your system and then run it.
- Enter the command for the scan you wish to do with extra targets or settings. For a TCP SYN scan, for instance, “nmap -s [target]”; for OS detection, “nmap -O [target].”
- Enter to run the scan.
- Nmap will show operating services, open ports, and a list of live hosts together with scan findings.
Top Functions Of Nmap With Codes
-
Network Mapping
Network mapping is Nmap’s primary purpose; it lets me scan the network and look for connected devices, including PCs, servers, routers, and switches. I find information on online devices, open ports, and network connections by running the basic Nmap command focused on an IP address or range. Zenmap allows one to depict this information graphically. Additionally captured by Nmap are media access control (MAC) addresses, which enable device manufacturer identification.
For example, I could run to find out which devices are linked to my network only running:
Code: nmap 192.168.1.0/24
-
Network Packet Manipulation
Nmap can change the contents of network messages. I can catch, filter, reroute, or send data packets with these tools. The Nping tool stands out because it can test firewall rules, stress test networks, and fix problems.
As an example, if I want to see how strong my network is, I could use
Code: nping –tcp -p 80 192.168.1.10
-
Scripting
The coding features of Nmap are what make it so powerful. I can automate complicated scanning jobs and find security holes with the Nmap Scripting Engine (NSE). To find weaknesses, for example, I might use
Code: nmap –script vuln 192.168.1.10
Fundamental Nmap Commands
I often run through these fundamental commands:
On a host, find open ports by:
- nmap <IP address>
To obtain OS details and service versions:
- Nmap -A <IP address>
To find whether a firewall is turned on.
- nmap -sA <IP address>
To examine a particular port in scanning
- nmap -p <port number> <IP address>
Nmap’s rich documentation offers many choices and examples for more complex scanning and scripting.
Looking for Alternatives to Nmap
As a security tester, I’ve looked into many tools that can be used instead of Nmap. There are several open-source tools for security testing, and each one is good at a different part of it:
- Zap: great program scanner.
- John the Ripper: A strong brute force password hacker.
- Wireshark: It is a flexible packet sniffer.
These tools are handy, but they usually only cover specific areas of security testing. On the other hand, Nmap is the best because it can scan whole networks.
Even paid penetration testing tools like Rapid7’s Metasploit or Burp Suite have difficulty entirely replacing Nmap. These paid tools have features and interfaces that are easy for anyone to use and can do various security jobs. However, Nmap is still used by many security teams, including mine, because it can run scripts and meet special user needs.
Nmap gets most of its money from OEM licensing, meaning companies buy and use it for their goods. Many paid pen-testing tools either use parts of Nmap code in their programs or run Nmap locally and then use their programs to read the results.
Sometimes, companies that buy commercial tools might use Nmap behind the scenes. Most of the time, the extra cost is worth it because these commercial tools are so easy to use that even IT security staff with little experience can do jobs that would be hard to do with Nmap alone. Also, these tools make it easier to write professional reports faster, which is a big plus.
It’s also possible for companies to use skilled penetration testing services instead of their tools. It’s essential to keep in mind, though, that some security testing firms may use the open-source Nmap tool directly. Most businesses are honest about how they work, but some, like Nmap Online, which has a name that could be confusing, use images and domain names that look a lot like those on the official Nmap.org website, which could lead to confusion.
Even though there are other options, I find that Nmap’s many features and adaptability make it an essential part of my security testing kit.
In Summary
In my toolkit for cybersecurity, Nmap is quite a helpful instrument. Although mastery requires time and effort, the great powers it provides make it well worth it. Nmap offers a complete collection of tools to help you safeguard and comprehend your network regardless of your knowledge about network security—that of a security professional, network administrator, or just curious learner.
FAQs
What is Nmap, and for what purposes can one utilize it?
For Network Mapper, Nmap is an open-source network security audit and discovery tool. It lets users scan networks looking for running services, open ports, live hosts, and operating systems. IT managers and cybersecurity experts extensively use Nmap for chores, including network inventory, host or service uptime monitoring, and timetable management of service upgrades.
How might I install Nmap on several OS systems?
Installing Nmap differs somewhat based on your operating system:
- Linux: Run sudo apt-get install nmap to install Nmap on variants such as Debian or Ubuntu. While the installation command may vary for other distributions, it is usually found in the default repositories.
- Windows: Download the installer from the official Nmap website, then run the executable file to install.
- macOS: Take advantage of Homebrew or another package manager. The installation command is brew install nmap.
- Zenmap: You can download the Zenmap graphical user interface (GUI) variant for a more aesthetically pleasing experience for all operating systems.
Can one legally use Nmap for network scanning?
While using Nmap is legal, the legality relies on your usage. A perfectly lawful and popular security audit and management method is scanning your network or one under clear authority. Using Nmap to scan devices or networks without permission is unethical and illegal. Always be sure you have the required rights before doing any scans since unauthorized scanning could result in serious legal penalties.